Flexible deployment options


Define pipeline routes as version-controlled code. Abstract makes it easy to automate pipeline creation, track changes, and scale across environments.

Define pipeline routes as version-controlled code. Abstract makes it easy to automate pipeline creation, track changes, and scale across environments.

Enrich telemetry events in‑stream with context like Geo‑IP, asset, identity and threat intelligence to add meaningful context before delivery to analytics systems.

Detect and mask sensitive fields in-stream, protecting personal data (PII protection) and aiding compliance with GDPR, HIPAA, PCI.

Switch destinations with ease using our drag-and-drop pipeline creation. Duplicate telemetry routes (e.g. to both on‑prem and cloud systems), validate parity, normalize and safely migrate over without data loss.

Normalize or reshape events and apply consistent schemas (e.g. Splunk CIM or OCSF), for downstream compatibility.

Transform and Aggregate events for performance: compress schemas, aggregate redundant alerts, sample intelligently to preserve value while reducing cost and alert fatigue.

Filter out noise, empty fields, duplicates and less‑valuable data to reduce ingestion and storage costs by 70–80 % on average.

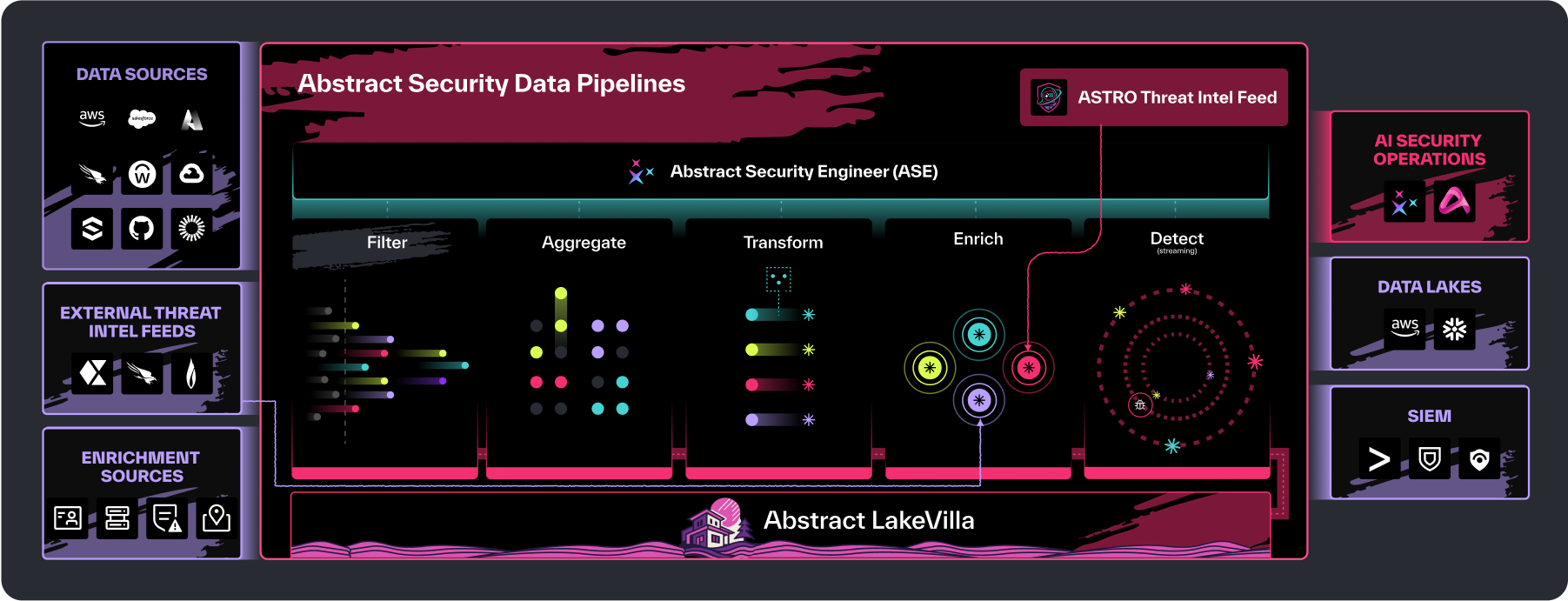
Route data from any source to any analytics engine or storage (e.g. SIEM, data lake, Abstract LakeVilla) with support for hundreds of integrations, enabling easy migrations and avoiding vendor lock‑in.

Abstract supports hundreds of integrations! Get unified visibility by integrating logs, events, threat intel feeds, across all data sources into a centralized platform for consistent monitoring, security analysis, and operations.
Detect adversary activity in real time using built-in threat intel from Abstract (powered by ASTRO) and your own feeds via integrated connectors—for faster, more accurate triage.

Detect adversary activity in real time using built-in threat intel from Abstract (powered by ASTRO) and your own feeds via integrated connectors—for faster, more accurate triage.

Abstract maps detections directly to ATT&CK techniques in real time. Teams get clear coverage, faster threat classification, and better reporting for audits and red team readiness.

Skip hours of writing complex queries. Abstract uses drag-and-drop logic enabling teams to create, test, and deploy detections quickly with zero ramp-up.

Build custom detection rules using your own logic and threat models with easy-to-use drag-and-drop blocks.

Use ready-to-run detection rules built and updated daily by Abstract’s ASTRO Team. Get high-fidelity, field-tested content Out-Of-The-Box from day one.

Cut Mean Time To Detect to seconds from hours! Abstract identifies threats the moment they appear in the stream - before they reach storage. Don't wait for indexing or query lag to find bad actors.

Create, assign, and close detection cases directly in Abstract. Track progress, set statuses, and retain context without needing to pivot between tools mid-investigation.

Abstract uses real-time Security Effectiveness Score so you can easily measure your detection coverage.

Filter low-fidelity signals at the stream level to suppress alert fatigue at the source. Abstract reduces false positives before they pollute your stack.
Separate real‑time signals from low‑value telemetry, and archive the rest in LakeVilla. You minimize SIEM spend while keeping long-term data instantly usable.

Separate real‑time signals from low‑value telemetry, and archive the rest in LakeVilla. You minimize SIEM spend while keeping long-term data instantly usable.

Bridge Past and Present Data Seamlessly. Maintain a single data fabric - from live streams to archived logs with uniform access across detection, hunting, and compliance workflows.

Meet Retention and Audit Needs! Store cold telemetry for compliance or traceability, instantly accessible for audits or investigations without operational overhead.

LakeVilla lives inside the Abstract architecture, route data with Abstract’s pipeline capability. No separate onboarding, ingestion paths or external tooling required to route data.

Retain Data on Your Terms! Filter, enrich, and shape data in real time before storage so you only keep what compliance or investigations require.

Eliminate Hidden Retrieval Costs! Avoid expensive retrieval or hidden fees - LakeVilla offers query-ready archival data without charging for retrieval.

Replay archived logs through live detection workflows to tune rules, hunt retrospectively, or validate past alerts.

Keep years of security telemetry in cost‑efficient cloud object storage through LakeVilla supported on AWS, Azure, or GCP, without performance trade‑offs.

Query cold, archived data instantly without rehydration or indexing delays. LakeVilla keeps logs searchable and actionable whenever needed.
Blend Analyst and AI Judgment. Use ASE interactively during detection creation and investigations. You retain control while ASE augments your expertise.

Blend Analyst and AI Judgment. Use ASE interactively during detection creation and investigations. You retain control while ASE augments your expertise.

ASE provides a complete attack narrative—who, what, where, when and how—by correlating multi-source events. ASE surfaces threat context in seconds.

Select multiple events and let ASE instantly stitch the story together — delivering a clear, concise summary without the noise.

ASE supports security investigations by allowing analysts to collect contextual information from a range of third-party data sources, including VirusTotal, URLQuery, Shodan, and security blogs.

Stop wasting time normalizing complex data sources, let ASE map source events to destination schemas for you.

Accelerate Triage and Response. Cut investigation time from minutes to seconds with instant event insights and prioritized threat context from ASE and quickly surfaces what matters most.

Turn Alerts into Insights Automatically. ASE speeds up understanding by giving analysts clear, natural-language summaries of the events, resources and context surrounding the detection.

Operating quietly in the background, ASE helps you navigate the complexity of enterprise security data with clarity and confidence.

With “Ask ASE” feature, get help creating search filters by asking in plain English.